Hatchet
About Hatchet
Hatchet is an AI-powered tool designed for incident responses in tech environments. It assists on-call engineers by triaging and investigating issues promptly, thereby reducing downtime. By integrating with various log systems, Hatchet automates the resolution process, maximizing efficiency and allowing teams to focus on critical services.
Hatchet offers competitive pricing plans tailored for businesses, focusing on tier-1 service needs. Plans provide unique functionalities and integrations, ensuring teams can automate incident responses effectively. Upgrading improves resolution speeds and enhances overall service reliability.
Hatchet boasts a user-friendly interface, tailored for seamless navigation and efficiency. Its organized layout ensures that on-call engineers can easily access necessary features, facilitating quick incident resolution while being visually appealing and intuitive for users of all technical levels.
How Hatchet works
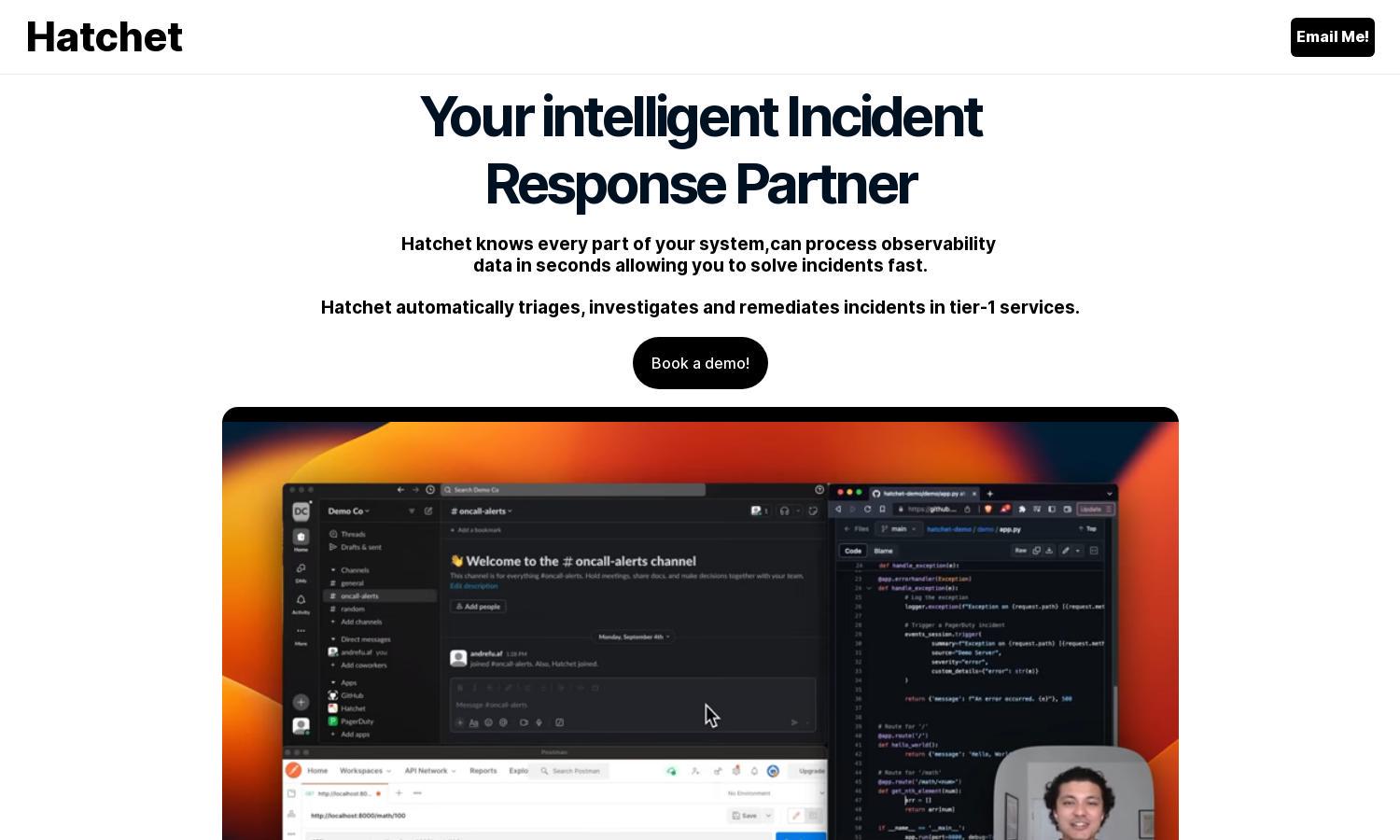
Users start by onboarding Hatchet and integrating it with their existing alerting systems. Once connected to the relevant log files, it automatically analyzes data during incidents. Its intuitive design guides users through triaging and suggests potential fixes, ensuring a streamlined investigation process that enhances workflow.
Key Features for Hatchet
Automated Incident Triage
Hatchet's automated incident triage feature empowers engineers to respond swiftly to incidents. By analyzing logs and suggesting actionable pathways, Hatchet enables teams to minimize downtime. This innovative functionality helps businesses maintain critical services and reduces the financial impact of outages.
AI-Driven Log Analysis
Hatchet leverages AI-driven log analysis to provide deep insights during incidents. This feature allows users to quickly pinpoint issues by scanning various log formats and making educated suggestions for fixes. The result is a faster resolution time and improved service reliability for businesses.
Self-Hosted Security
Hatchet ensures data security through its self-hosted model, training on-premises and eliminating telemetry. This unique advantage guarantees that sensitive information stays within the user’s infrastructure, providing peace of mind and compliance with privacy standards.
You may also like: