Threat Watch
Instantly assess your cybersecurity health with Threat Watch for actionable insights on compromised accounts and devi...
Visit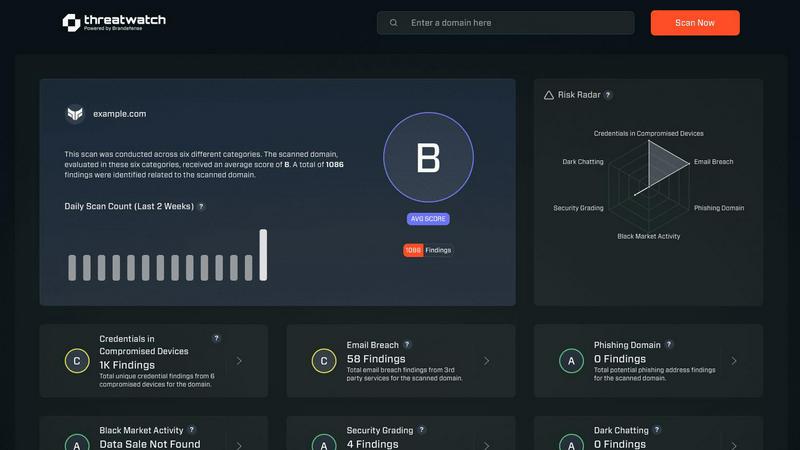
About Threat Watch
Threat Watch is a cutting-edge cybersecurity intelligence solution tailored for organizations of all sizes seeking to enhance their security posture. By analyzing key assets, vulnerabilities, and exposures, Threat Watch provides a comprehensive view of your cyber health. Designed for IT administrators, security teams, and compliance officers, this powerful tool allows users to uncover critical security insights quickly. Its primary value proposition lies in its ability to deliver real-time insights and automated assessments, enabling organizations to identify, prioritize, and mitigate risks effectively. With features such as compromised credential monitoring, detection of breached accounts, and dark web content analysis, Threat Watch empowers organizations to act swiftly against potential threats and safeguard their digital environments.
Features of Threat Watch
Comprehensive Vulnerability Assessment
Threat Watch conducts thorough assessments of your organization’s vulnerabilities, providing detailed reports that highlight potential weaknesses. This feature helps organizations prioritize their security efforts based on risk levels and potential impact.
Real-Time Threat Intelligence
Stay ahead of cyber threats with Threat Watch's real-time threat intelligence. This feature continuously monitors various digital channels to provide timely updates on emerging threats, allowing organizations to respond proactively and mitigate risks before they escalate.
Breached Account Monitoring
With the Breached Account Monitoring feature, Threat Watch scans known data breaches to identify if any of your organization's accounts have been compromised. This proactive approach ensures that vulnerabilities are addressed before they can lead to significant security incidents.
Dark Web Monitoring
Threat Watch includes Dark Web Monitoring, which searches for your organization's sensitive data on illicit online platforms. By identifying potential leaks or stolen information, this feature helps organizations take immediate action to protect their assets and reputation.
Use Cases of Threat Watch
Incident Response Planning
Organizations can leverage Threat Watch to enhance their incident response plans. By understanding vulnerabilities and potential threats, security teams can develop tailored response strategies that minimize damage during a cyber incident.
Compliance Assurance
For businesses that must adhere to regulatory standards, Threat Watch assists in maintaining compliance by providing insights into security weaknesses. This feature helps organizations implement necessary controls and demonstrate compliance to auditors effectively.
Risk Management
Threat Watch is an essential tool for risk management, allowing organizations to evaluate their cybersecurity landscape continuously. By identifying high-risk areas, organizations can allocate resources effectively to strengthen their defenses.
Employee Training and Awareness
Utilizing insights from Threat Watch, organizations can develop targeted training programs for employees. By educating staff about the latest phishing tactics and compromised accounts, companies can foster a culture of security awareness and vigilance.
Frequently Asked Questions
What types of organizations can benefit from Threat Watch?
Threat Watch is designed for organizations of all sizes, including small businesses, large enterprises, and government agencies, providing tailored cybersecurity solutions to meet diverse needs.
How does Threat Watch integrate with existing security tools?
Threat Watch is built with compatibility in mind, allowing seamless integration with various existing security tools and platforms, enhancing overall cybersecurity operations without disrupting workflows.
Is there a trial version available for Threat Watch?
Yes, Threat Watch offers a free scan that allows potential users to evaluate the platform's capabilities before committing to a subscription. This helps organizations understand the value of the solution.
How frequently does Threat Watch update its threat intelligence?
Threat Watch updates its threat intelligence in real-time, ensuring that users receive the most current information regarding vulnerabilities and emerging threats, enabling timely responses to potential risks.
You may also like:
finban
Plan your liquidity so you can make decisions with confidence: hiring, taxes, projects, investments. Get started quickly, without Excel chaos.
Zignt
Zignt simplifies contract management with secure templates, automated sharing, and real-time signing for seamless col...
aVenture
aVenture is an AI-driven platform for in-depth research on private companies, investors, and market trends.